Restrict Access with IAM Service
Best practice: Avoid using the Root User. Instead, create IAM Users with minimal permissions needed to manage resources. This makes management easier and reduces security risks.
In this section, we will create a policy to restrict a user to only interact with EC2 Instances in the ap-southeast-1 region.
1. Access the AWS IAM Management Console
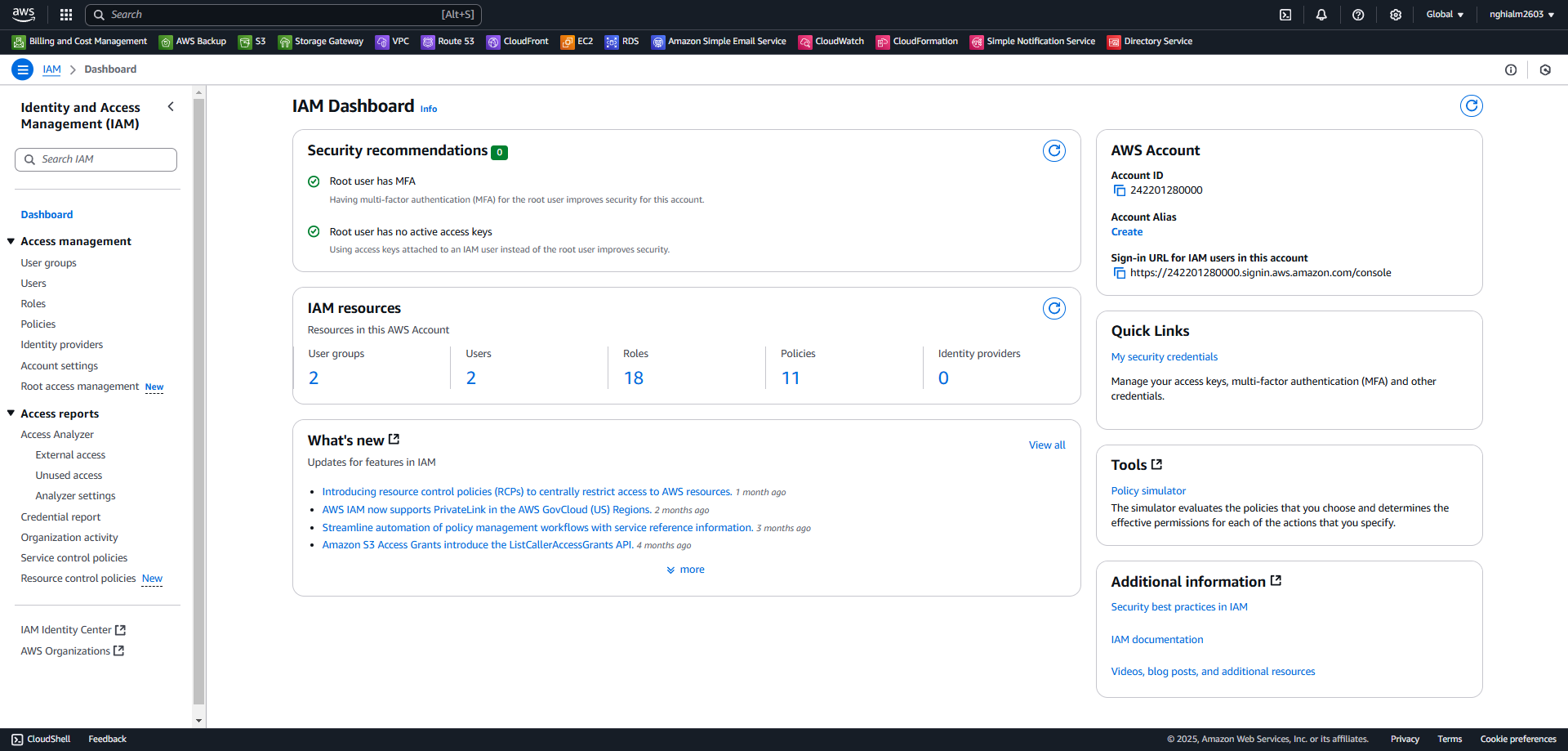
2. Create Custom Policies
2.1. On the left navigation menu, select Policies.
2.2. In the Policies interface, click Create policy.
2.3. Step 1 - Specify permissions:
- Go to the JSON tab, paste the following JSON into the Policy Editor, and click Next.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": "ec2:*",
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:RequestedRegion": "ap-southeast-1"
}
}
}
]
}
This JSON allows interactions with EC2 resources but only in the ap-southeast-1 region.
2.4. Step 2 - Review and Create:
Provide a name and description for the policy.
Click Create policy.
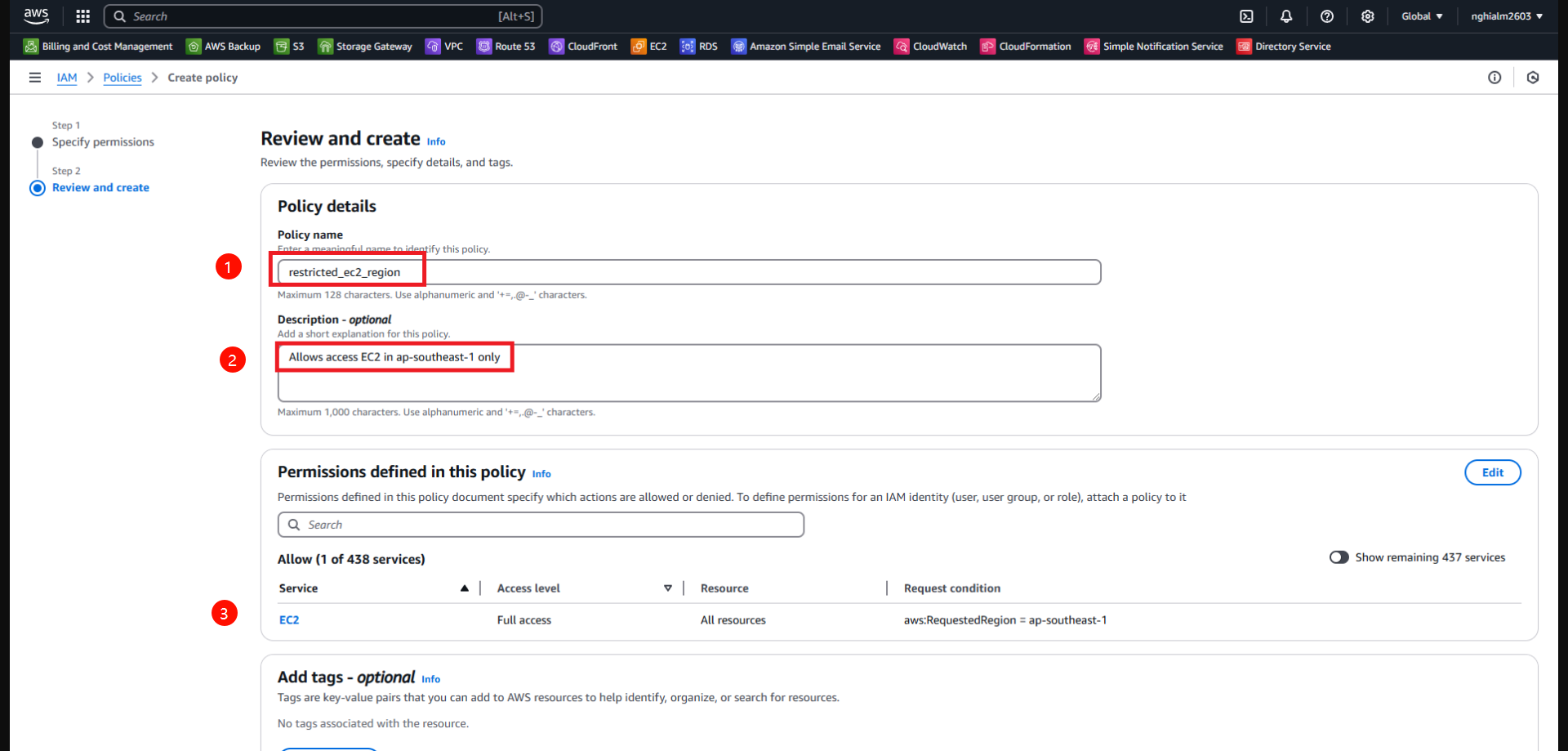
3. Create a User Group and Assign the Policy
To reuse the above policy, assign it to an IAM Group. All IAM Users in the group will share the same permissions.
3.1. Access User groups from the left navigation menu.
3.2. In the User groups interface, click Create group.
3.3. In the Create user group interface:
- Name the group and assign the custom policy created earlier.
- Click Create user group.
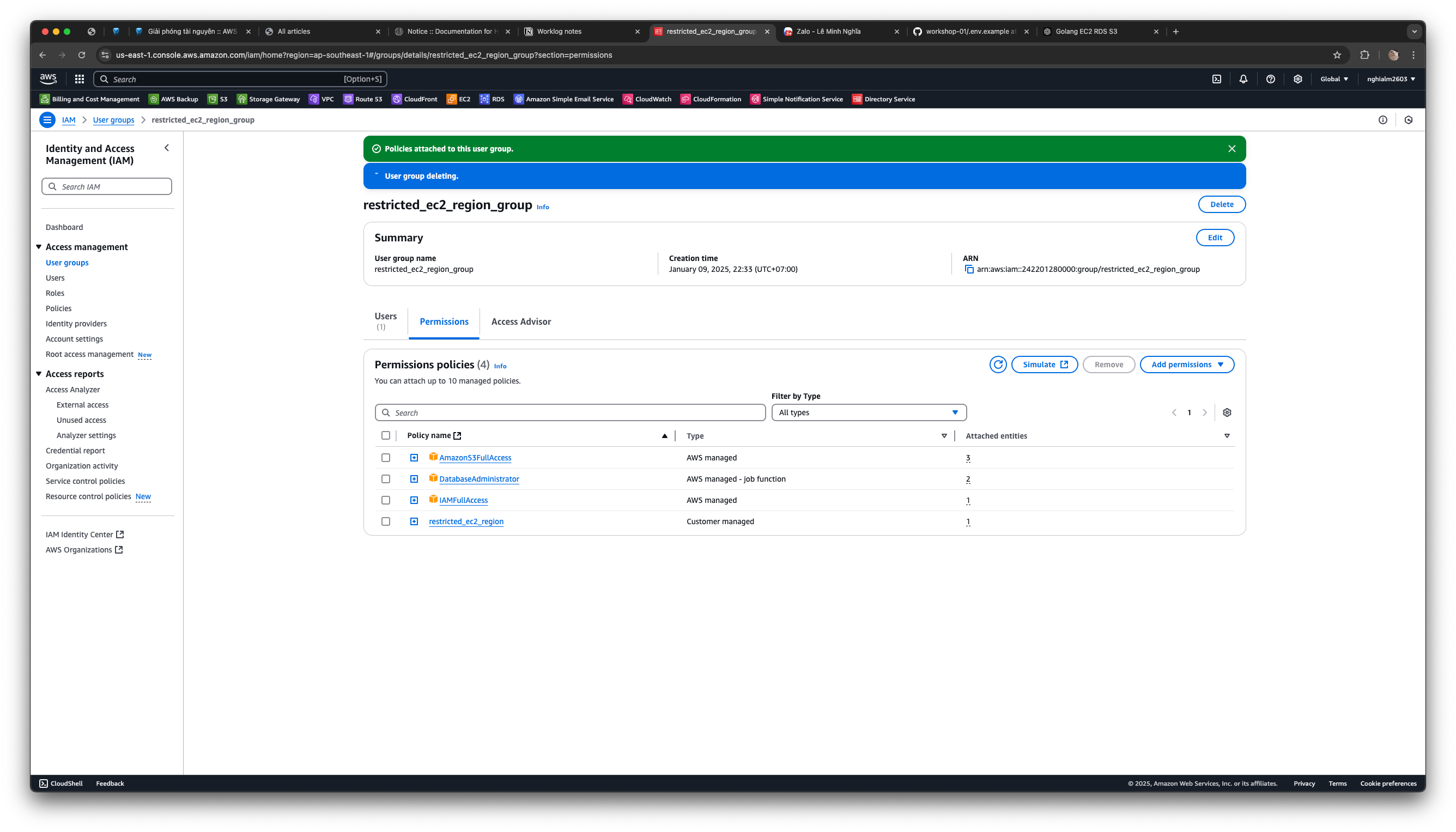
4. Create a User and Assign Them to the Group
4.1. Access Users from the left navigation menu.
4.2. Click Create user.
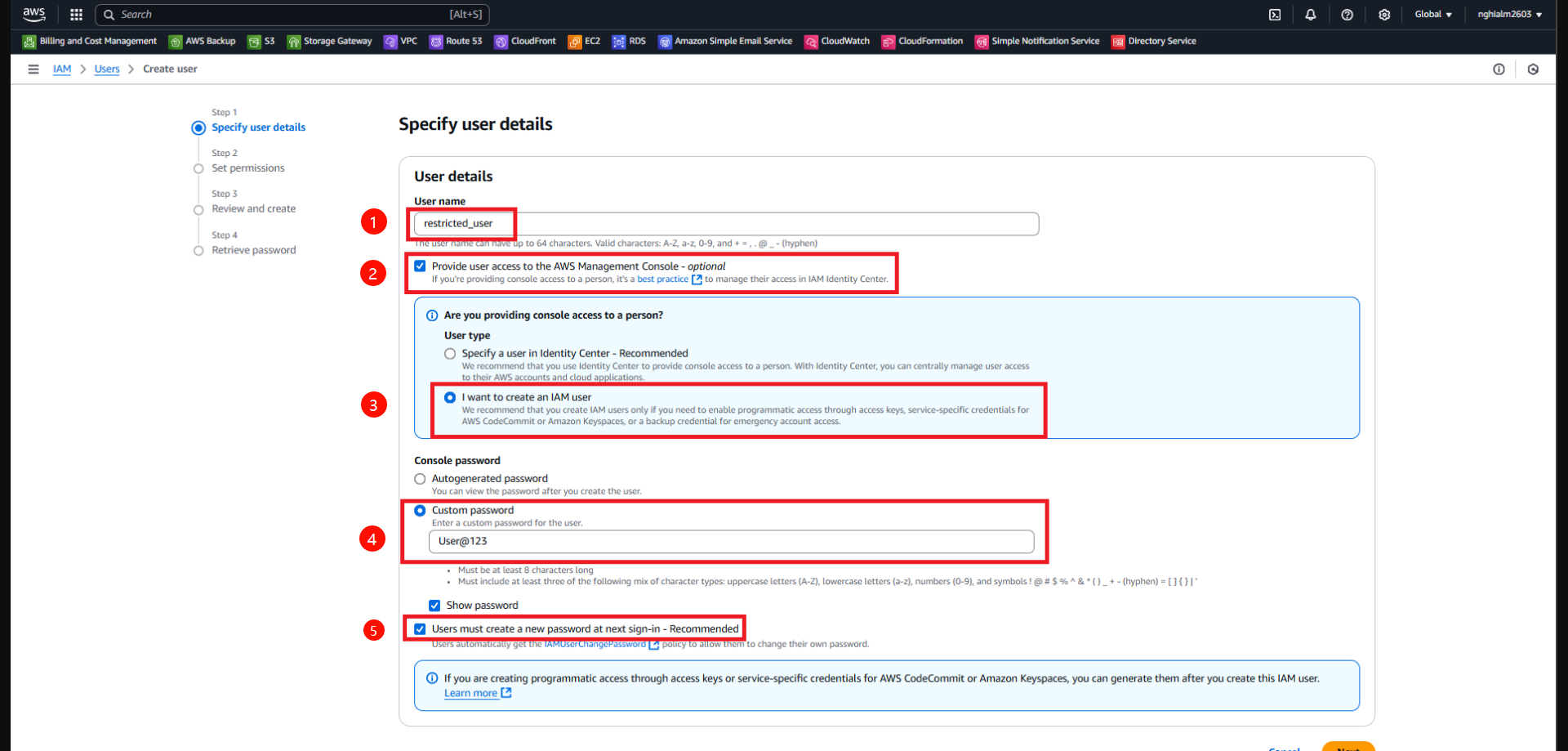
4.3. Step 1 - Specify user details:
- Enter a username.
- Select Provide user access to the AWS Management Console.
- Choose I want to create an IAM user.
- Set a custom password.
- Click Next.
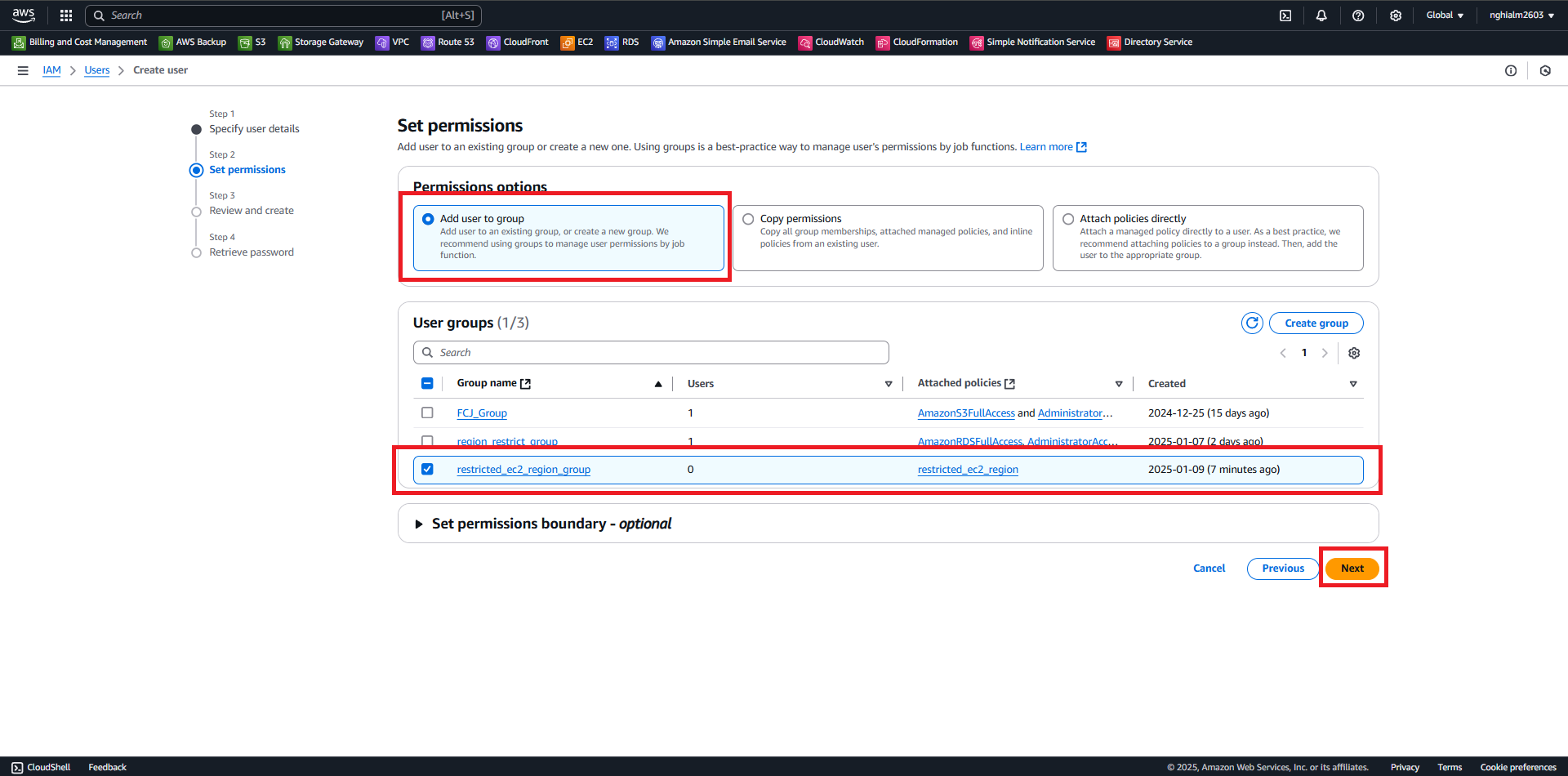
4.4. Step 2 - Set permissions:
- Select Add user to group.
- Choose the group created earlier (e.g., restricted_ec2_region_group).
- Click Next.
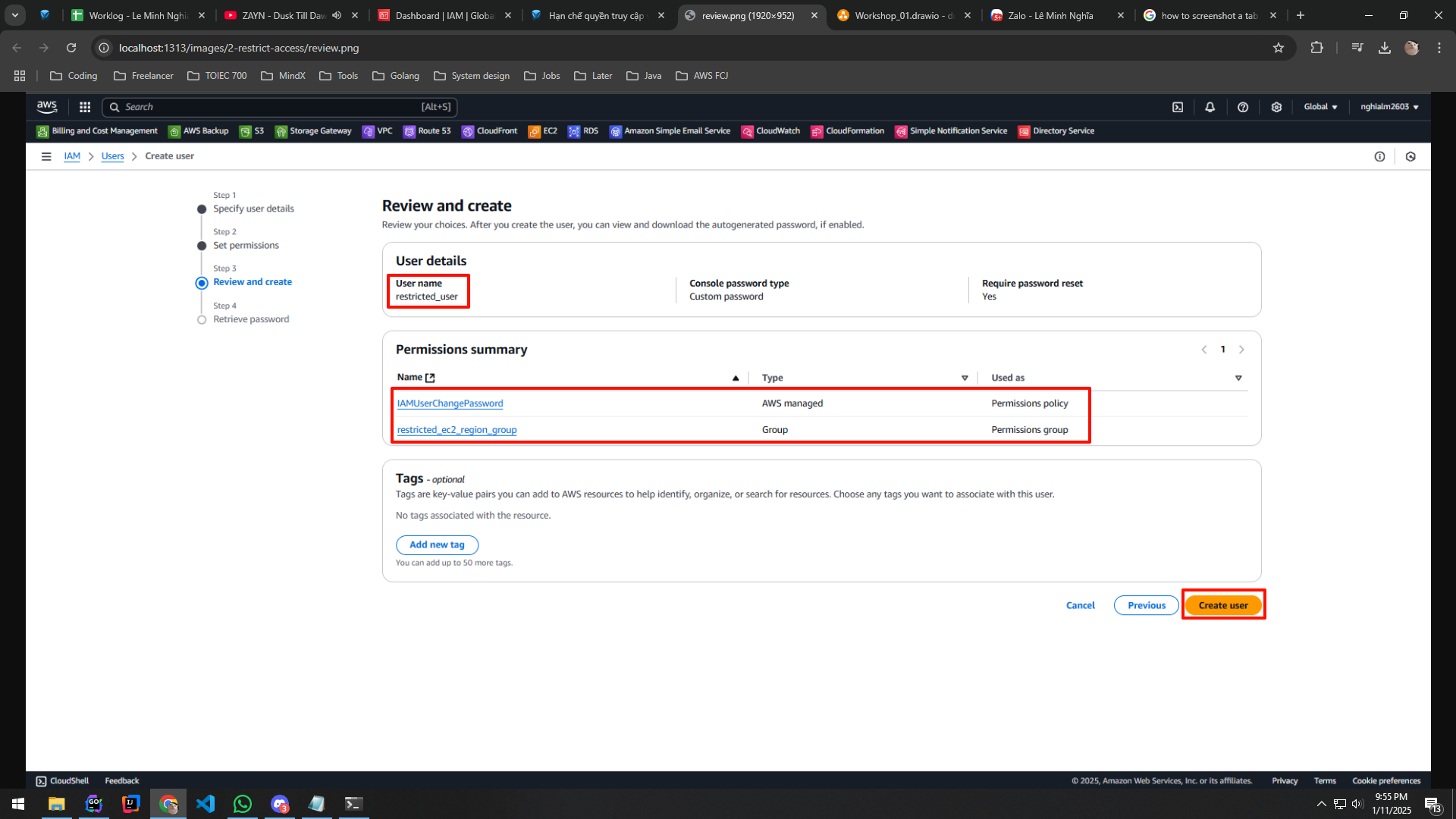
4.5. Step 3 - Review and Create:
- Review the user and permissions.
- Click Create user.
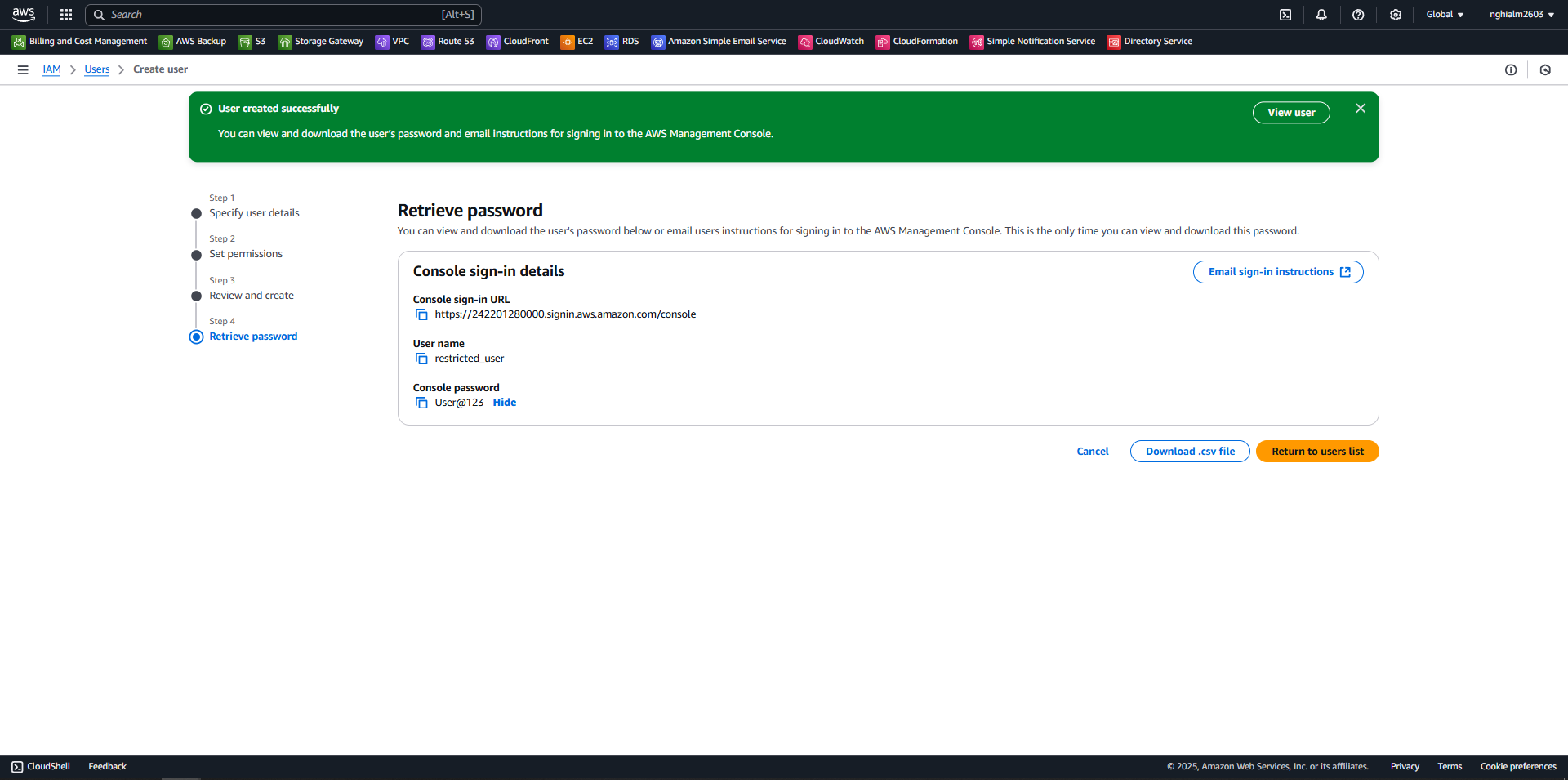
4.6. Step 4 - Retrieve password:
- Save or download the .csv file to manage user credentials.
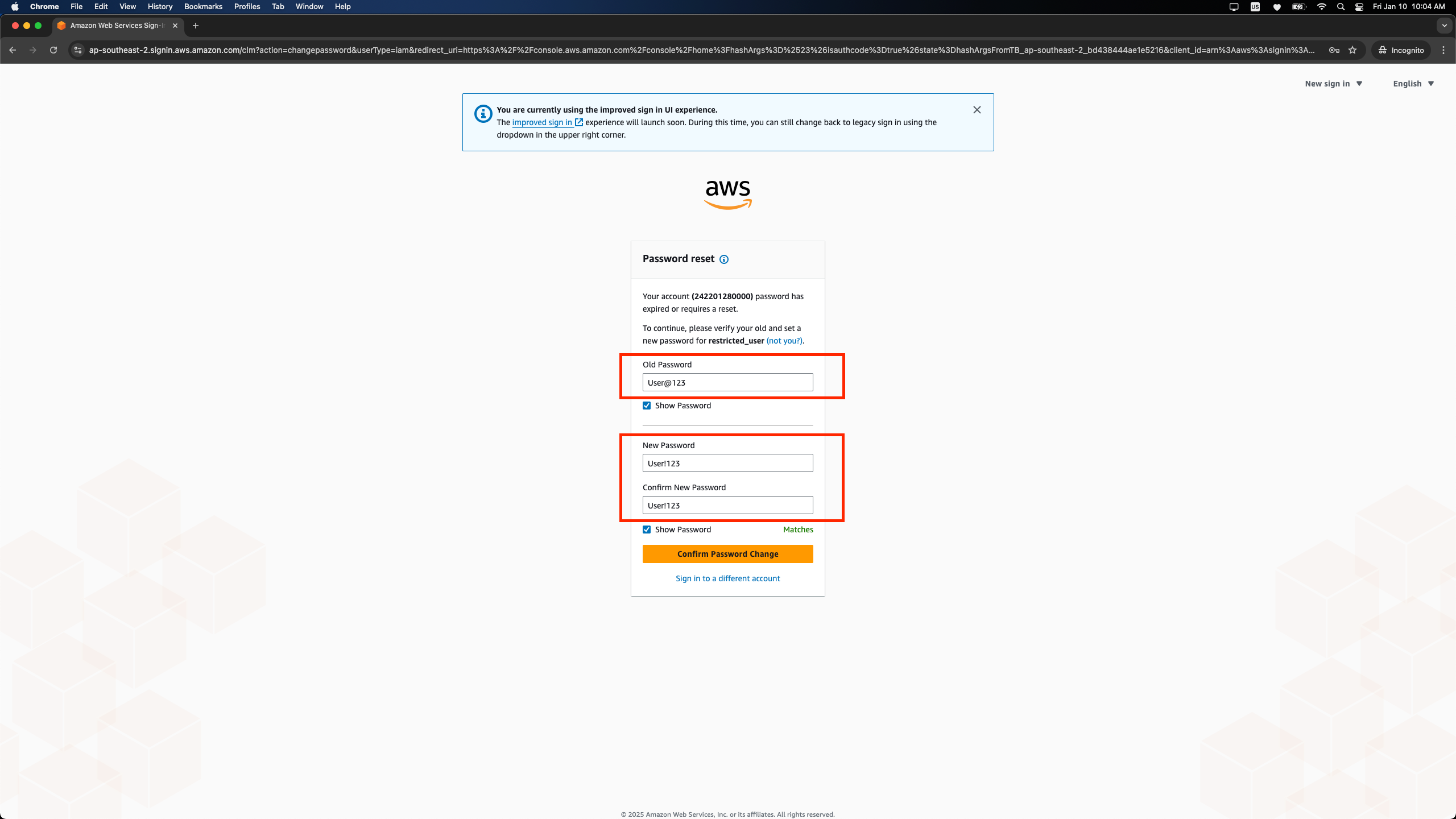
4.7. Log in as the IAM User:
- Copy the sign-in URL.
- Log in using the username and password.
- Update the password when prompted.
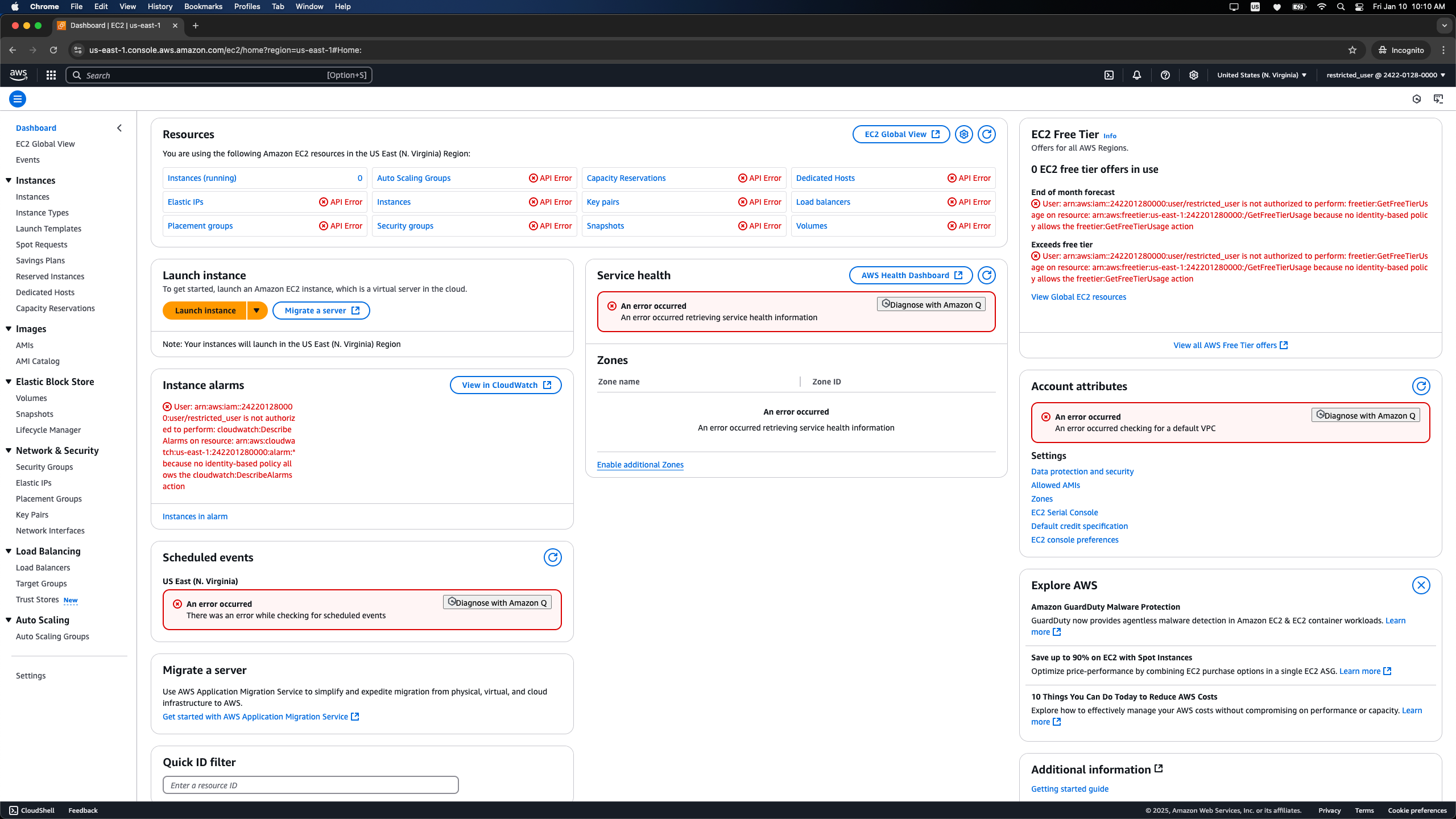
Testing:
Check the EC2 service in us-east-1: The policy should restrict access in this region.
Check the EC2 service in ap-southeast-1: Access should be allowed.