Team Access
Group Access
- Burnham Team, only having access to resources in their dedicated namespace along with a demonstration of how we can use Kubernative native construct to ensure that only people used in team-burnham namespace can access those resources. This is also known as soft multi-tenancy you are using Kubernetes constructs like namespaces, quotas, and network policies to prevent applications from being accessed. implementations in different namespaces communicate with each other.
kubectl describe role -n team-burnham
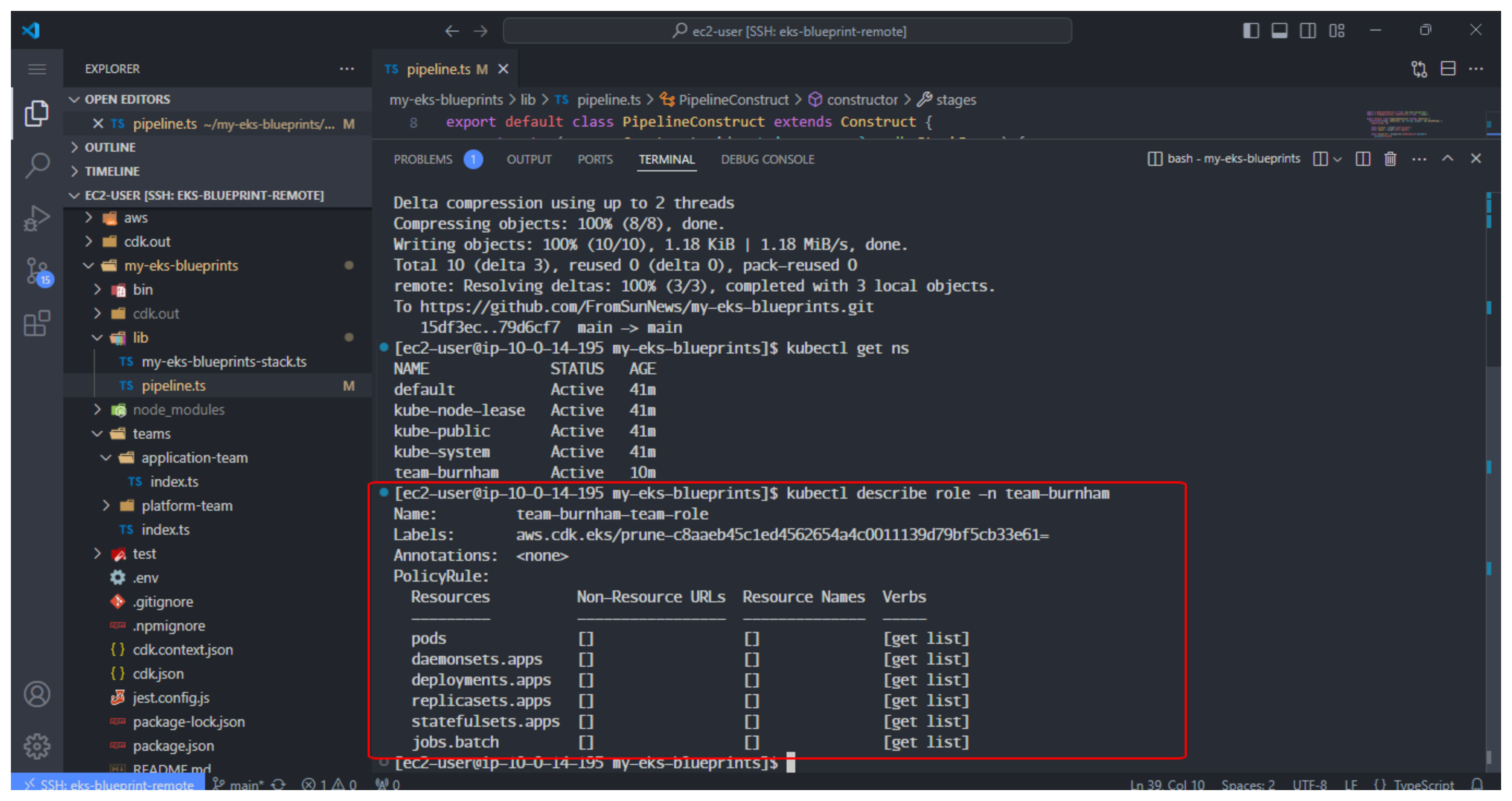
You can see that Team Burnham can only get and list a set of application-focused Kubernetes resources (pods, daemonsets, deployments, replicasets, statefulsets, and jobs). You’ll notice that they don’t have permission to create or delete resources in their respective namespaces.
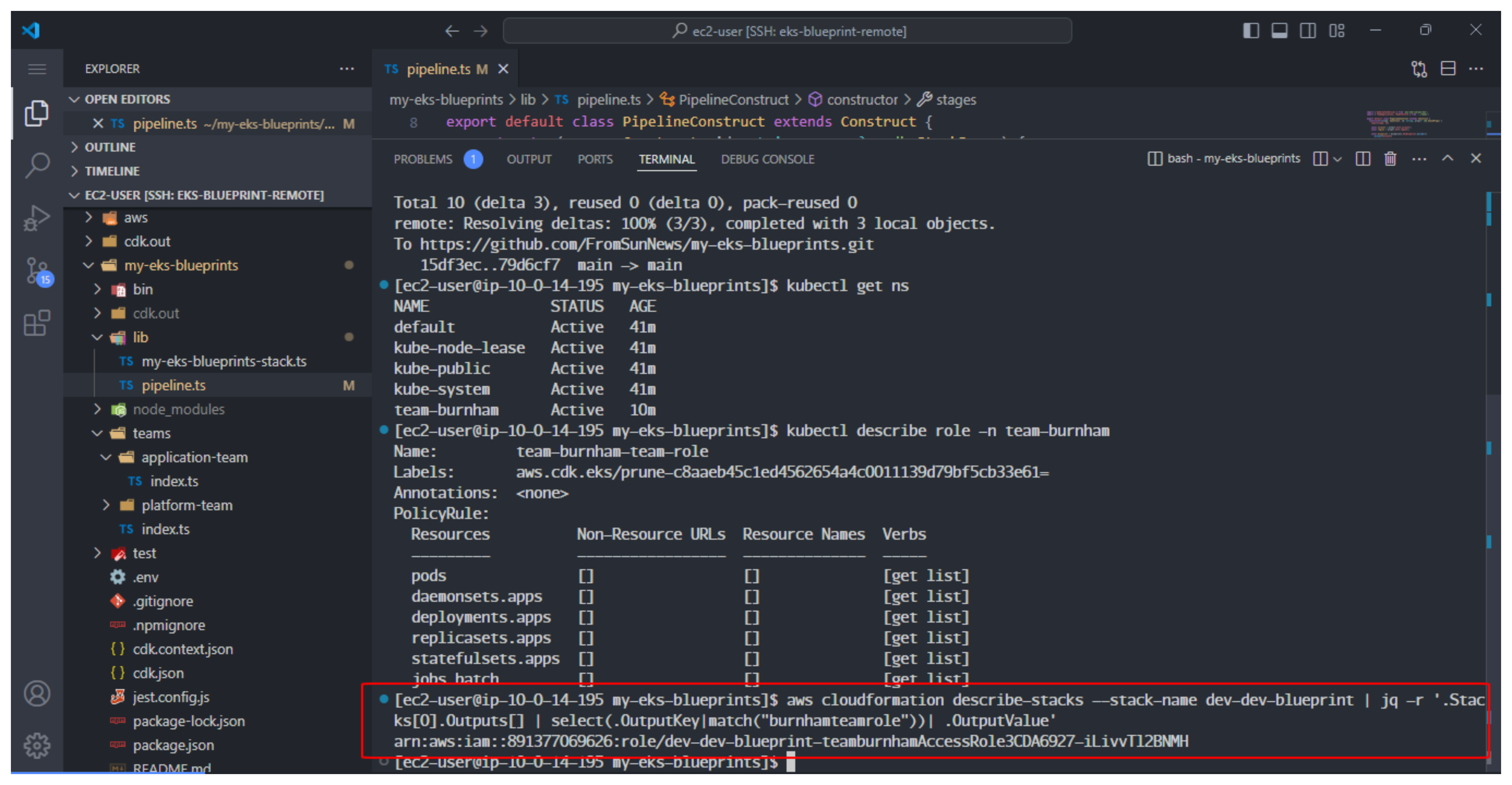
- Retrieve the created role for Team burnham by running the following command:
aws cloudformation describe-stacks --stack-name dev-dev-blueprint | jq -r '.Stacks[0].Outputs[] | select(.OutputKey|match("burnhamteamrole"))| .OutputValue'
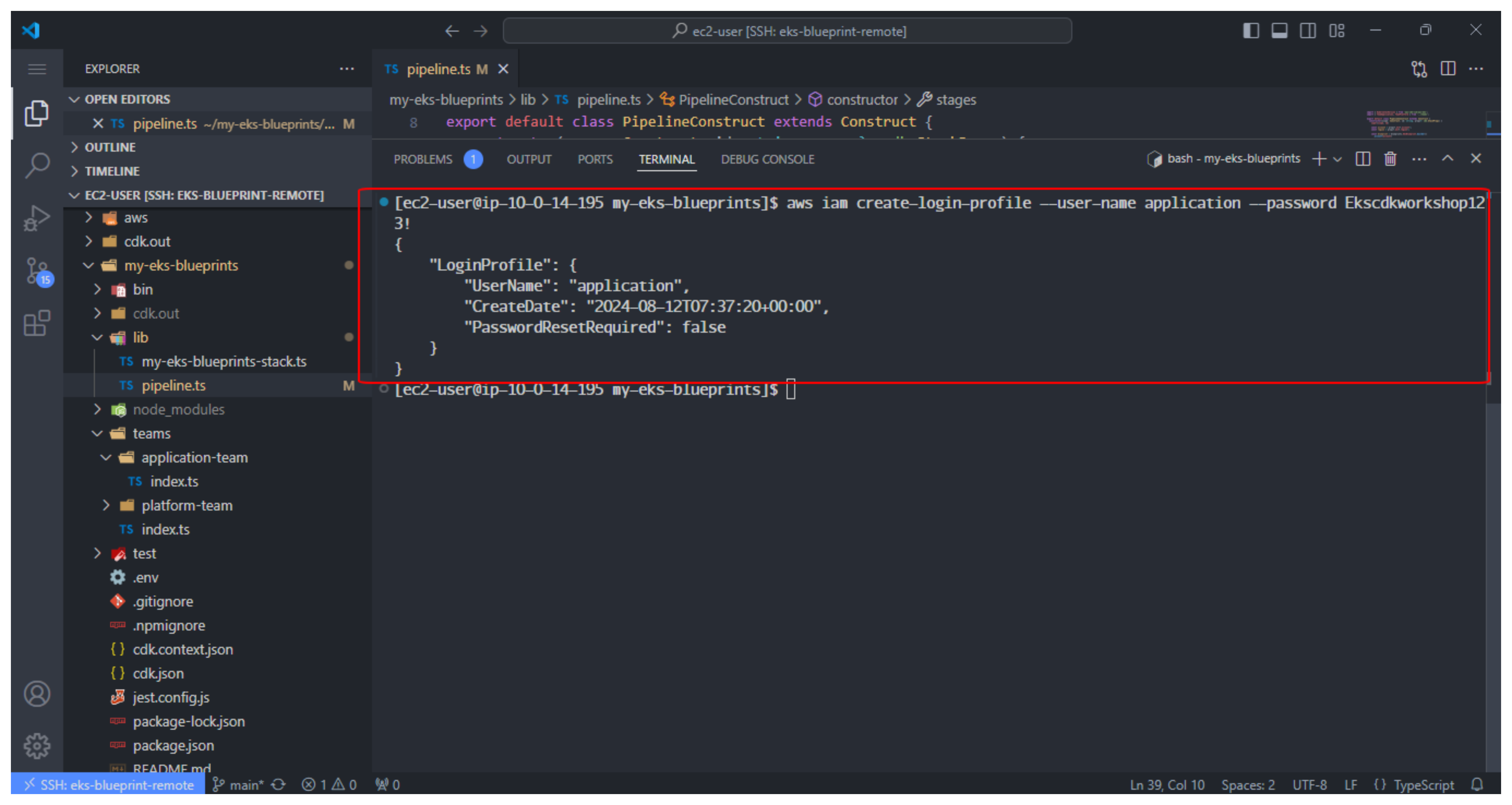
- Create credentials for application
aws iam create-login-profile --user-name application --password Ekscdkworkshop123!
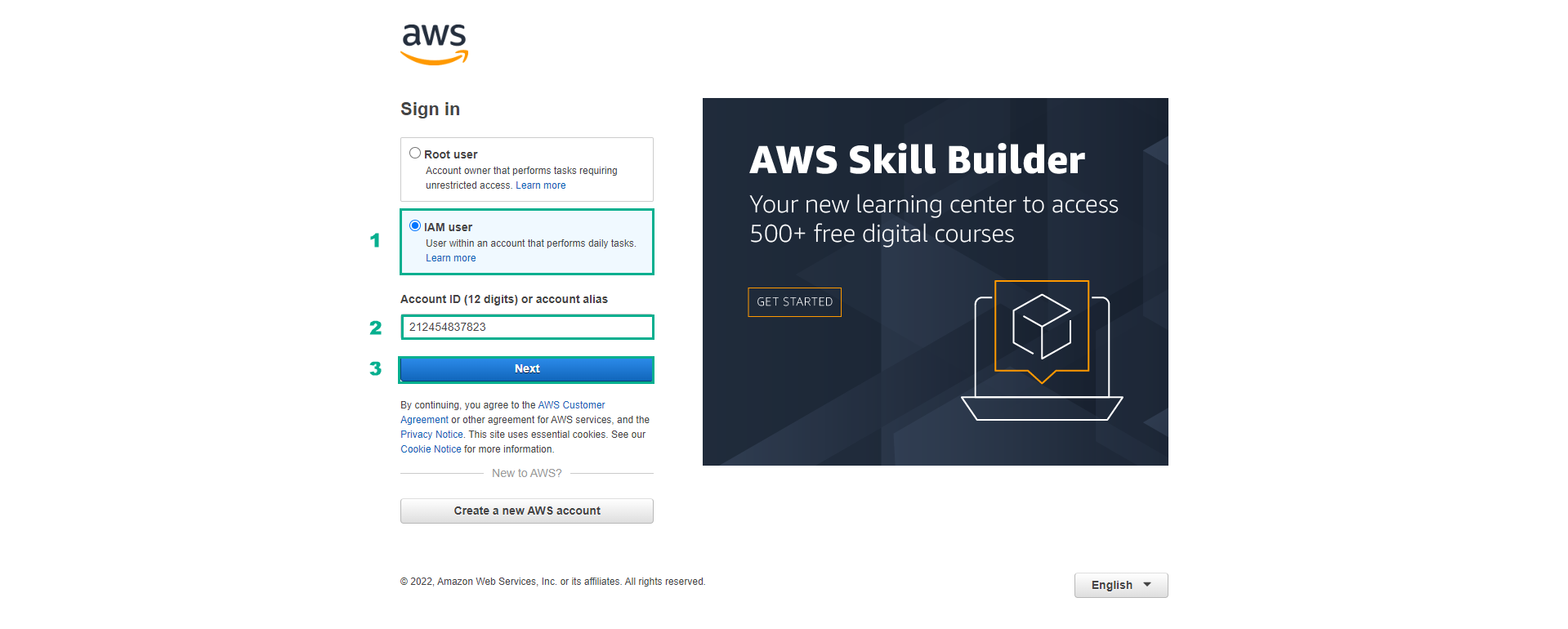
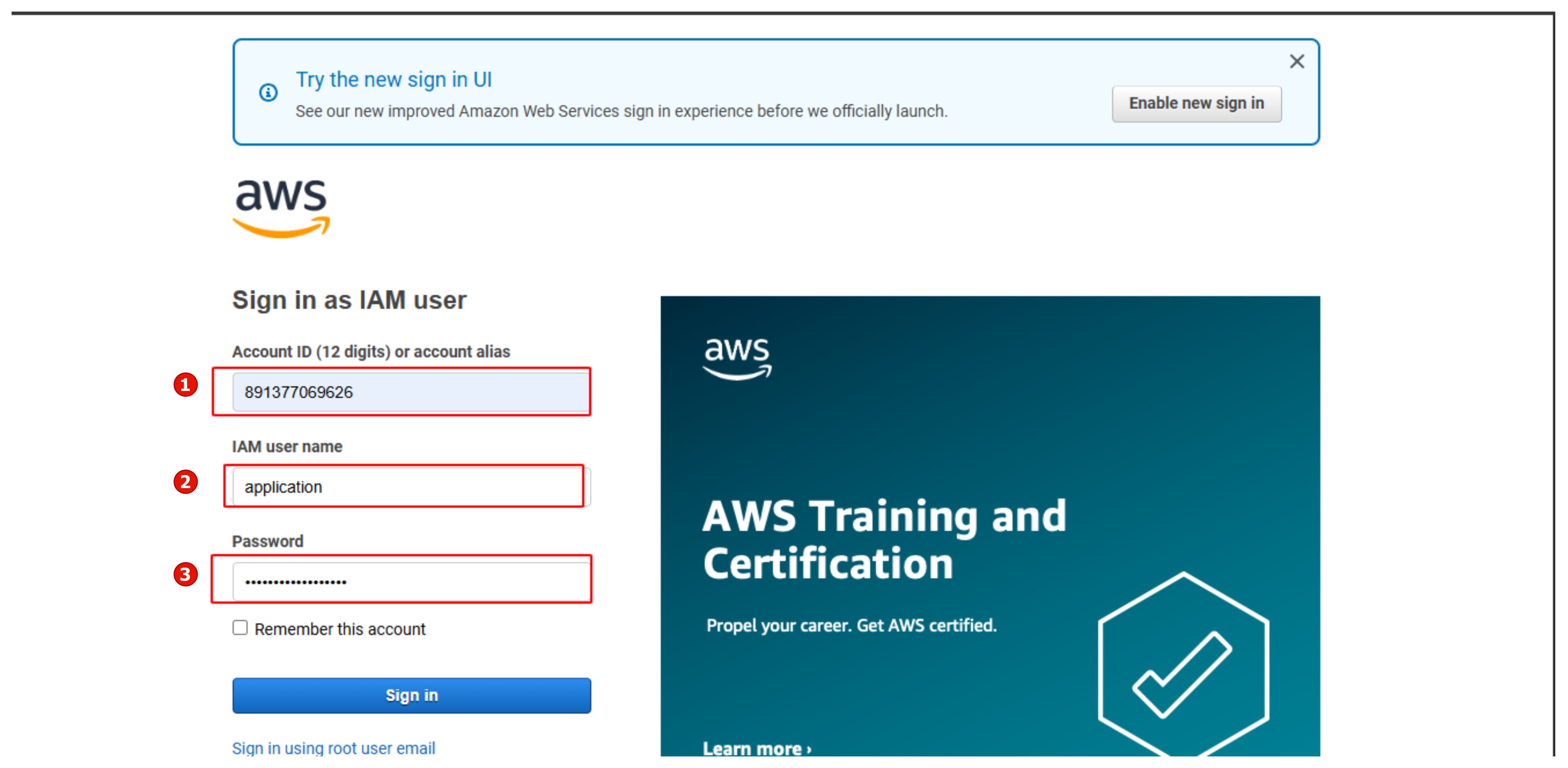
Go to AWS
- Perform login with IAM user
- Enter your Account ID
- Select Next
Next,
- Enter IAM user name as application
- Enter password just created
- Select Sign in
- Complete the login
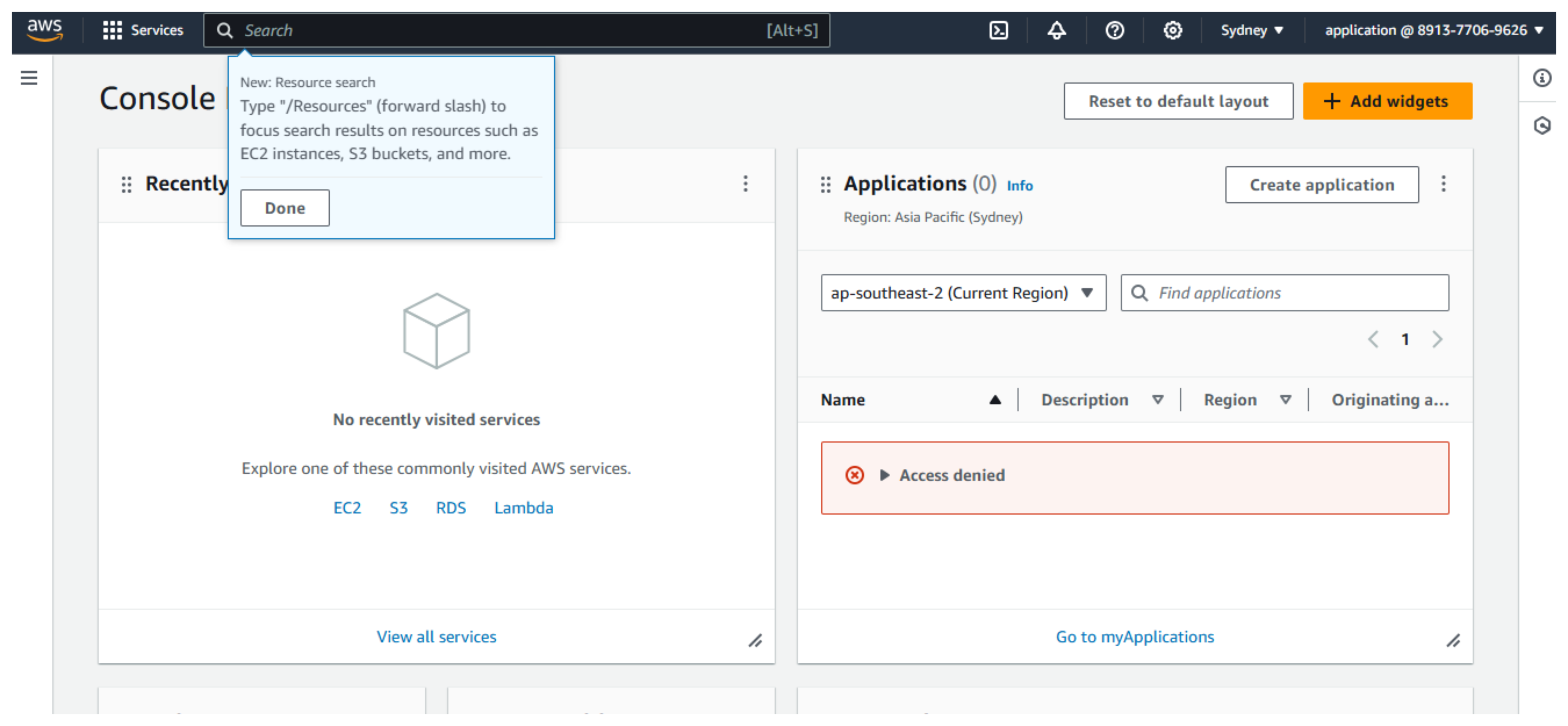
In the AWS interface
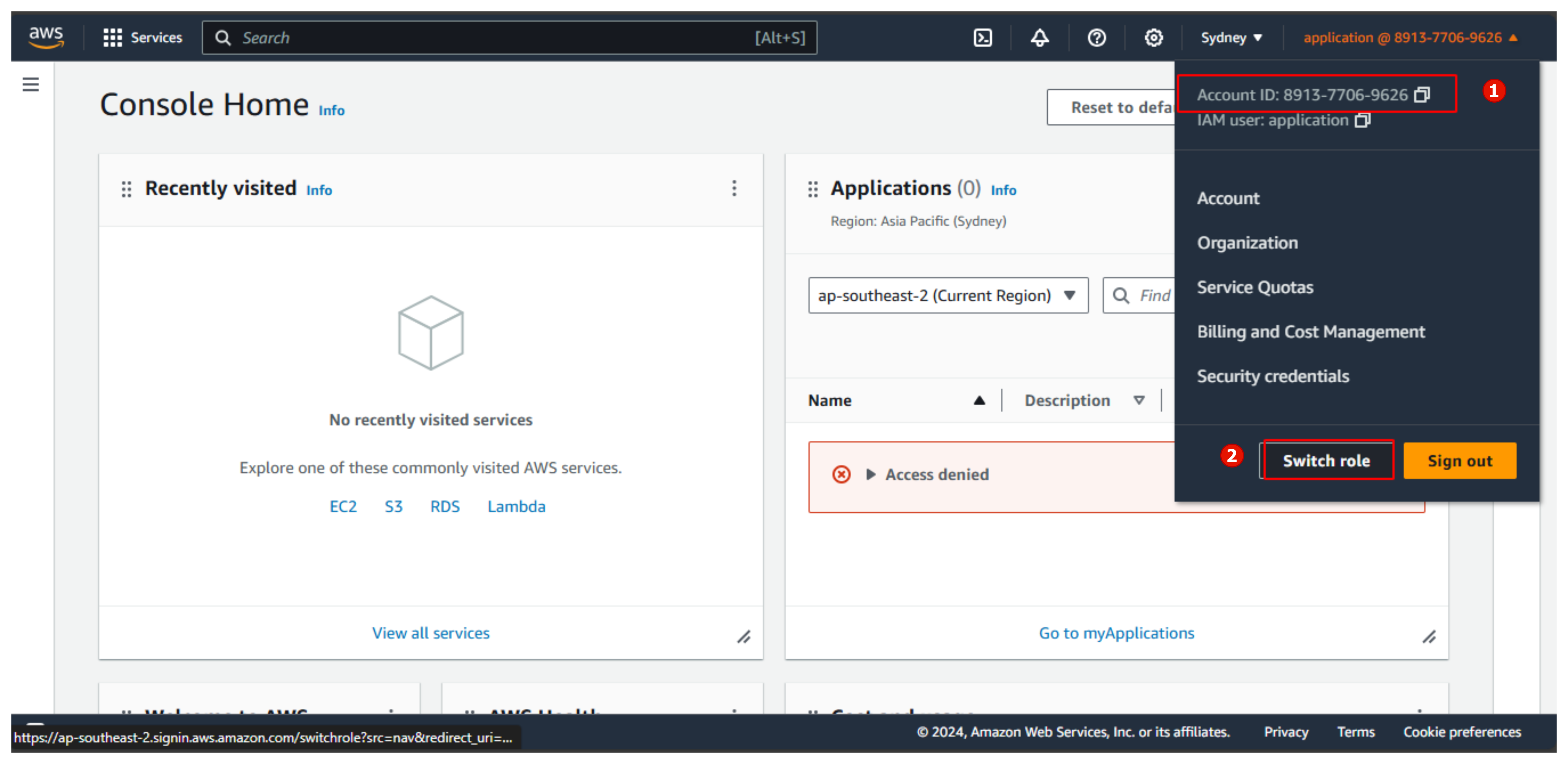
- Select Switch role
In the Switch Role interface
- Account, enter your Account ID
- Then enter Role
- Select Switch Role
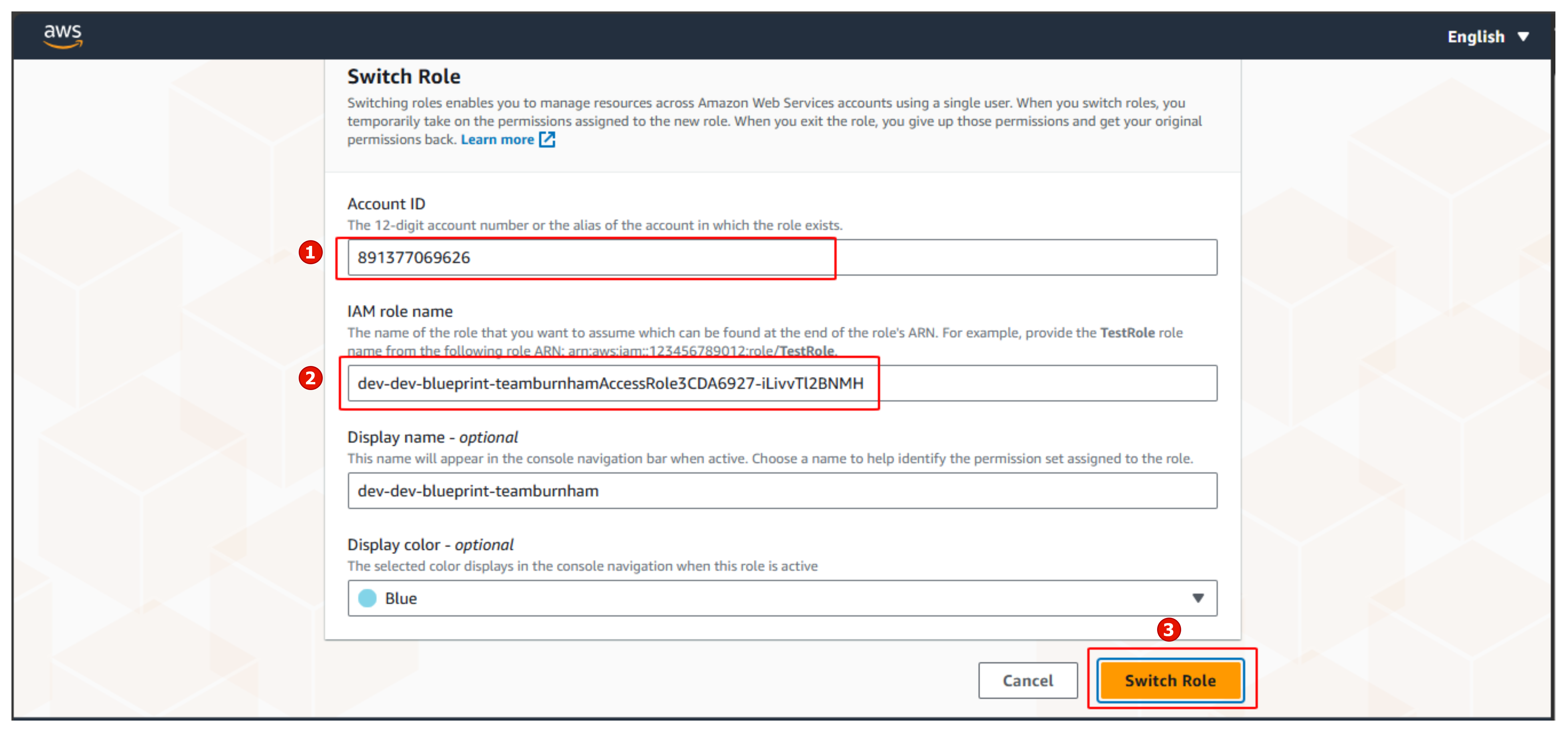
- Complete Switch Role
- Access to EKS
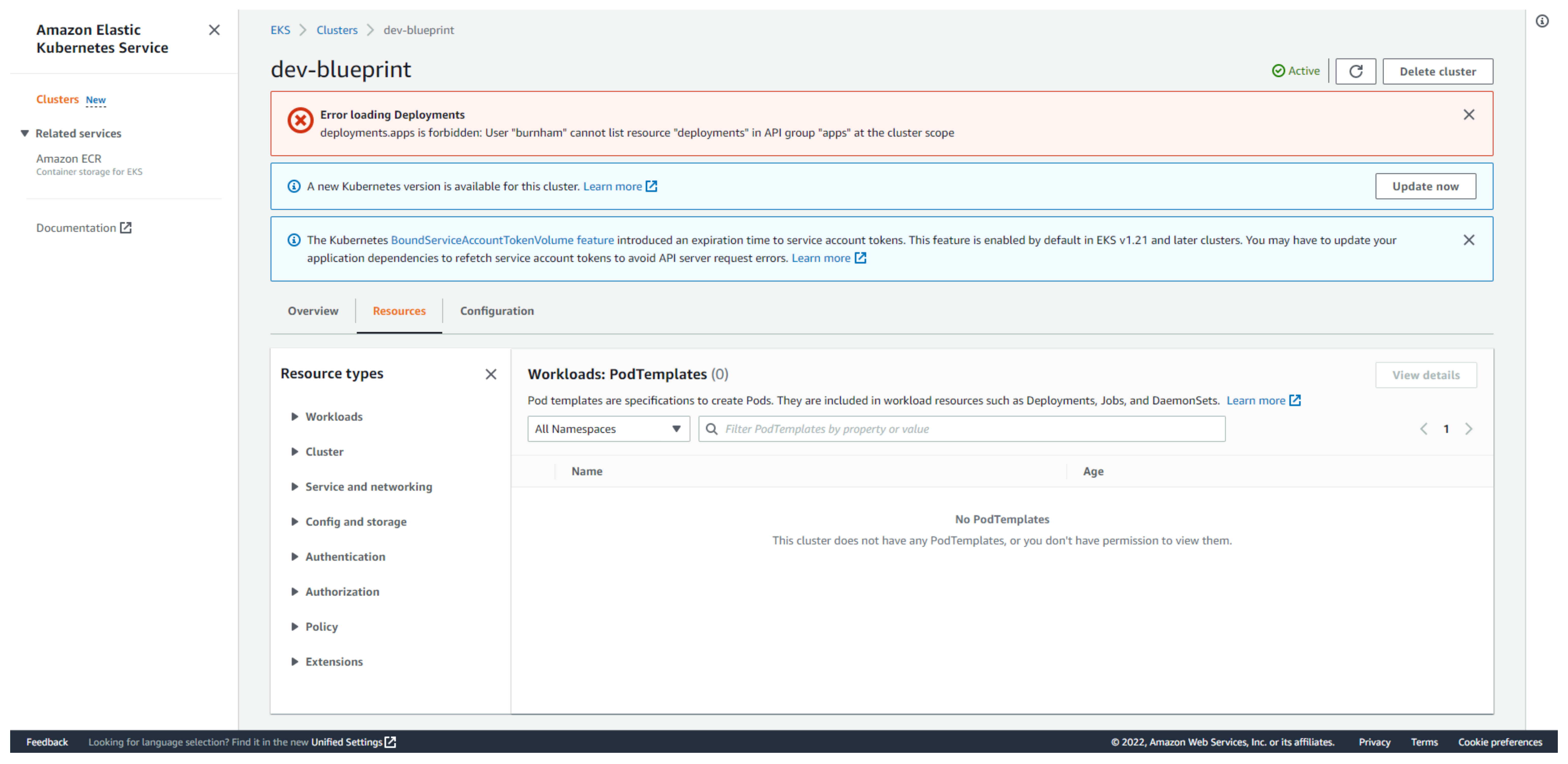
- Here you will see an error message stating that the Team Burnham user is NOT allowed to list deployments in all namespaces.
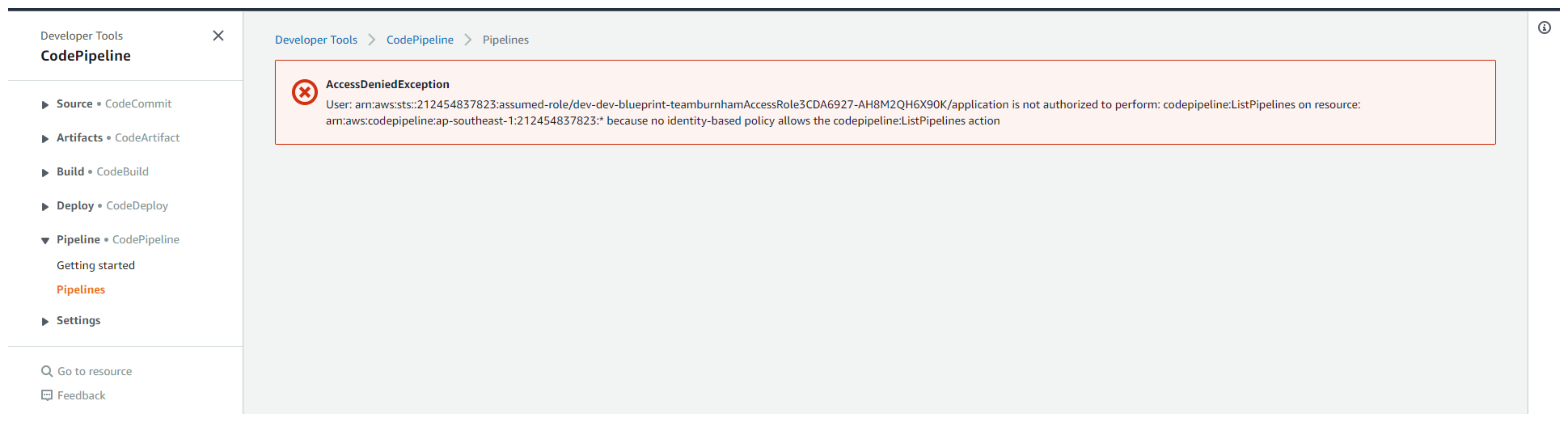
- When you select team-burnham in namespace, you will see the forbidden message disappear. This means that you are currently showing Team Burnham workloads (no workloads since any workloads have not been deployed).